
- Information Security Policy
-
Information Security Organization And Management

Information Security Organization And Management
The core significance of information security for ITE is to provide stable and secure information systems required for the company's operations, ensuring the availability, accuracy, and confidentiality of information.
Information Security Organization
The information security of the company is managed by the Information Security Responsible unit, Information Security Group, established at the end of 2022. This group includes a convener, an information security manager, and information security personnel. The convener, who is the General Manager, is responsible for approving the execution scope and policies of the information security system and regularly reports to the Board of Directors. The information security officer is responsible for formulating information security policies and objectives, reporting regularly to the convener. Information security personnel are tasked with planning and implementing the company's information security system.
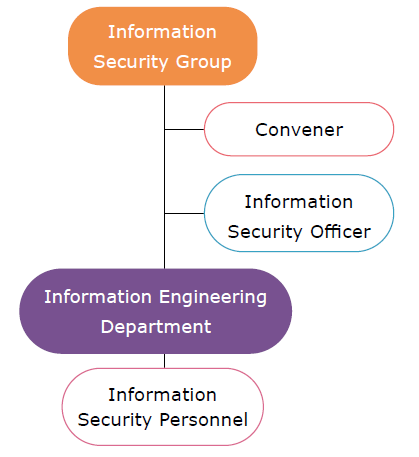
Specific management plans and resources invested in information security management
With the rapid advancement of the information age, convenience comes with unforeseen security risks. Severe incidents can paralyze the company's information network, interrupt operations, and cause data destruction or theft, leading to significant damage to the company and its stakeholders. The Information Security Group, following annual plans and goals, allocates budgets and implements protective mechanisms. These measures are complemented by employee training and awareness campaigns to strengthen security concepts, ensuring uninterrupted operations and protecting important confidential information of the company and stakeholders (customers, suppliers, etc.).
Information Security Protection Mechanism Implementation Items
| Endpoint Protection | Comprehensive endpoint protection systems are established for employee computer equipment and network gateway devices, with regular updates and vulnerability scans. |
| Cyberattack Defense | New generation firewalls and network behavior detection systems are installed, supported by strict network access control and two-factor authentication. Backup mechanisms are in place to prevent cyberattack and ensure availability. |
| Data Backup and Recovery | In addition to server virtualization and off-site/cloud backups, critical operational systems have established DR sites. These provide comprehensive data protection mechanisms for disaster recovery, with regular drills to ensure uninterrupted operations. |
| Strengthening Security Awareness | Regular awareness campaigns aligned with current security incidents and supplemented by social engineering exercises to reinforce employees' security concepts. |
Information Security Education and Training
In addition to system-level protection mechanisms, employees' information security awareness is the last line of defense for the company's information security protection. Besides, providing information security education for new employees, the company also regularly conducts awareness campaigns and announcements about popular information security incidents. Additionally, social engineering drills are conducted semi-annually to strengthen employees' information security awareness and implementation in their daily work.
To continually enhance the company's information security capabilities, investments in information security protection will continue in 2024. Plans include implementing the SIEM platform and NDR response module to achieve automated defense, enabling immediate detection and protection against various security attacks. The frequency of social engineering exercises will increase to once per quarter to heighten daily vigilance among employees. This aims to prevent damages from ransomware caused by employees accidentally clicking on phishing emails or from hackers infiltrating and stealing confidential company information, which could lead to financial and reputational losses for the company.

Data Building
We are currently preparing. Stay tuned!
PRIVACY POLICY
CLOSE








